Researchers on Tuesday disclosed a new espionage campaign that resorts to destructive data-wiping attacks targeting Israeli entities at least since December 2020 that camouflage the malicious activity as ransomware extortions.
Cybersecurity firm SentinelOne attributed the attacks to a nation-state actor affiliated with Iran it tracks under the moniker “Agrius.”
“An analysis of what at first sight appeared to be a ransomware attack revealed new variants of wipers that were deployed in a set of destructive attacks against Israeli targets,” the researchers said. “The operators behind the attacks intentionally masked their activity as ransomware attacks, an uncommon behavior for financially motivated groups.”
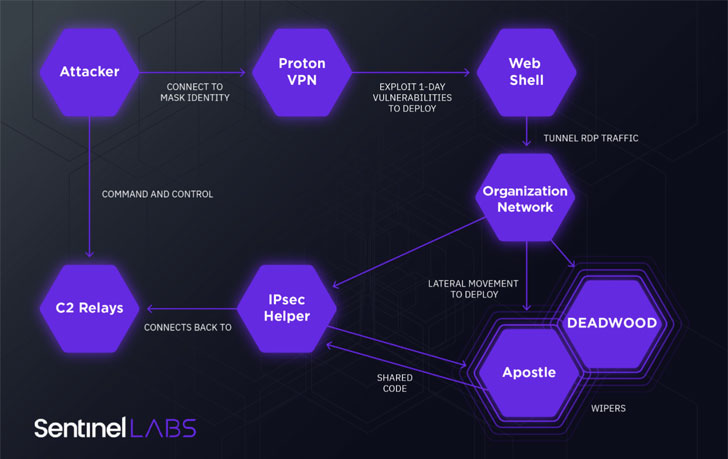
The group’s modus operandi involves deploying a custom .NET malware called Apostle that has evolved to become fully functional ransomware, supplanting its prior wiper capabilities, while some of the attacks have been carried out using a second wiper named DEADWOOD (aka Detbosit) after a logic flaw in early versions of Apostle prevented data from being erased.
In addition, the Agrius actors drop a .NET implant called IPsec Helper that can be used to exfiltrate data or deploy additional malware. What’s more, the threat actor’s tactics have also witnessed a shift from espionage to demanding ransoms from its victims to recover access to encrypted data, only to have them actually destroyed in a wiping attack.
Besides using ProtonVPN for anonymization, the Agrius attack cycle leverages 1-day vulnerabilities in web-based applications, including CVE-2018-13379, to gain an initial foothold and subsequently deliver ASPXSpy web shells to maintain remote access to compromised systems and run arbitrary commands.
If anything, the research adds to evidence that state-sponsored actors with ties to the Iranian government are increasingly looking at ransomware operations as a subterfuge technique to mimic other financially motivated cybercriminal ransomware groups.
Recently leaked documents by Lab Dookhtegan revealed an initiative called “Project Signal” that linked Iran’s Islamic Revolutionary Guard Corps to a ransomware operation through a contracting company.
“While being disruptive and effective, ransomware activities provide deniability, allowing states to send a message without taking direct blame,” the researchers said. “Similar strategies have been used with devastating effect by other nation-state sponsored actors.”