A new botnet named Orchard has been observed using Bitcoin creator Satoshi Nakamoto’s account transaction information to generate domain names to conceal its command-and-control (C2) infrastructure.
“Because of the uncertainty of Bitcoin transactions, this technique is more unpredictable than using the common time-generated [domain generation algorithms], and thus more difficult to defend against,” researchers from Qihoo 360’s Netlab security team said in a Friday write-up.
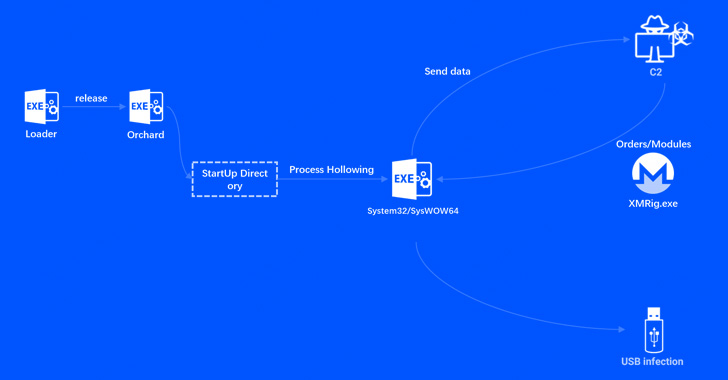
Orchard is said to have undergone three revisions since February 2021, with the botnet primarily used to deploy additional payloads onto a victim’s machine and execute commands received from the C2 server.
It’s also designed to upload device and user information as well as infect USB storage devices to propagate the malware. Netlab’s analysis shows that over 3,000 hosts have been enslaved by the malware to date, most of them located in China.
Orchard has also been subjected to significant updates in over a year, one of which entails a brief tryst with Golang for its implementation, before switching back to C++ in its third iteration.
On top of that, the latest version incorporates features to launch a XMRig mining program to mint Monero (XMR) by abusing the compromised system’s resources.
Another change relates to the use of the DGA algorithm employed in the attacks. While the first two variants exclusively rely on date strings to generate the domain names, the newer version uses balance information obtained from the cryptocurrency wallet address “1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa.”
It’s worth pointing out that the wallet address is the miner reward receiving address of the Bitcoin Genesis Block, which occurred on January 3, 2009, and is believed to be held by Nakamoto.
“Over the past decade or so, small amounts of bitcoin have been transferred to this wallet on a daily basis for various reasons, so it is variable and that change is difficult to predict, so the balance information for this wallet can also be used as DGA input,” the researchers said.
The findings come as researchers took the wraps off a nascent IoT botnet malware codenamed RapperBot that has been spotted brute-forcing SSH servers to potentially carry out distributed denial-of-service (DDoS) attacks.