An ongoing malicious campaign that employs phony call centers has been found to trick victims into downloading malware capable of data exfiltration as well as deploying ransomware on infected systems.
The attacks — dubbed “BazaCall” — eschew traditional social engineering techniques that rely on rogue URLs and malware-laced documents in favor of a vishing-like method wherein targeted users are sent email messages informing them of a forthcoming subscription charge unless they call a specific phone number.
By tricking the recipients into calling the number, the unsuspecting victims are connected with actual human operators at the fraudulent call centers, who then provide them with instructions to download the BazaLoader malware.
BazaLoader is a C++ downloader malware with the ability to install various types of malicious programs on infected computers, including deploying ransomware and other malware and stealing sensitive data from victimized systems. First observed in April 2020, BazaLoader campaigns have been used by multiple threat actors and frequently serves as a loader for disruptive malware, including Ryuk and Conti ransomware.
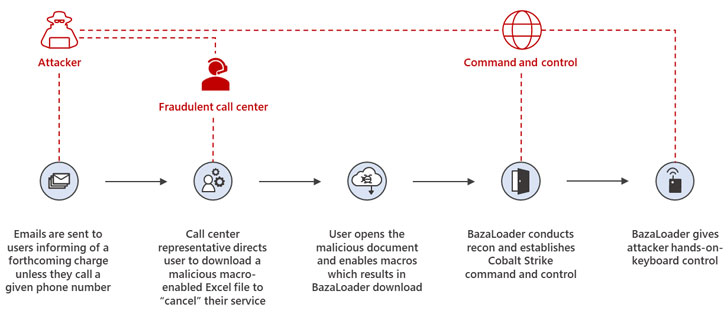 |
| BazaCall Attack Flow |
“Attacks emanating from the BazaCall threat could move quickly within a network, conduct extensive data exfiltration and credential theft, and distribute ransomware within 48 hours of the initial compromise,” Microsoft 365 Defender Threat Intelligence Team said in a report published Thursday.
Because the malware isn’t distributed via a link or document within the message body itself, the lures add a level of difficulty that enables attackers to evade phishing and malware detection software. This campaign is part of a broader trend in which BazaLoader-affiliated criminals in which they use call centers — the operators seemingly non-native English speakers — as part of an intricate attack chain.
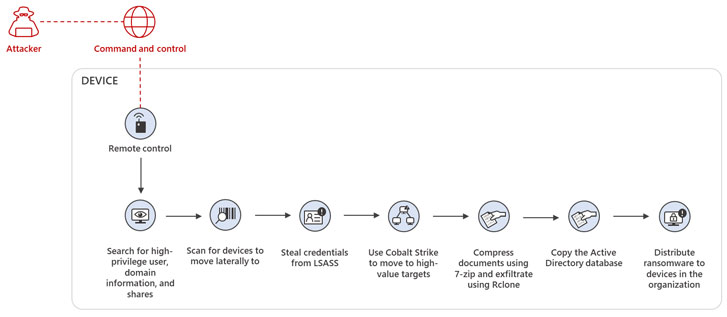 |
| Post-Compromise Activities |
Earlier this May, Palo Alto Networks and Proofpoint revealed an elaborate infection mechanism that leveraged fake ebooks (World Books) and movie streaming subscription services (BravoMovies), using the websites as a stepping stone to deliver a rigged Excel spreadsheet containing the BazaLoader malware. The latest attack disclosed by Microsoft is no different in that the call center agent serves as a conduit, urging the caller to navigate a recipe website (“topcooks[.]us”) in order to cancel the non-existent trial subscription.
“The use of another human element in BazaCall’s attack chain through the above mentioned hands-on-keyboard control further makes this threat more dangerous and more evasive than traditional, automated malware attacks,” the researchers said. “BazaCall campaigns highlight the importance of cross-domain optics and the ability to correlate events in building a comprehensive defense against complex threats.”


